Automated Reverse Engineering using Machine Learning
Main Article Content
Abstract
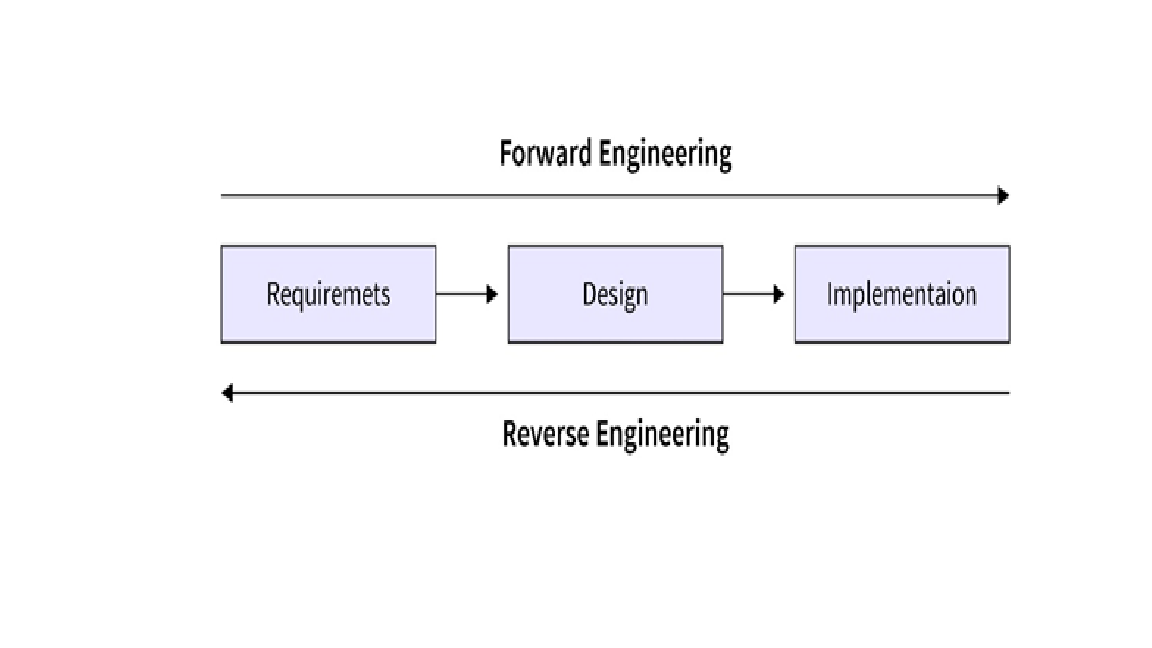
Reverse engineering plays a critical role in software security analysis, malware detection, and legacy system understanding. Traditionally, reverse engineering is a manual, time-consuming process that requires deep expertise in low-level code analysis and system architecture. However, recent advances in machine learning (ML) have opened new possibilities for automating various stages of the reverse engineering workflow. This paper explores the application of ML techniques—such as deep learning, sequence modeling, and graph-based learning—for automating tasks like binary classification, function identification, code decompilation, and behavior prediction. By leveraging large-scale code datasets and advanced feature extraction methods, ML models can learn patterns in binary structures and recover high-level insights from low-level machine code. The study demonstrates that ML-driven reverse engineering not only accelerates the analysis process but also enhances accuracy and scalability, making it a valuable tool for security researchers and analysts. Experimental results show promising performance across multiple reverse engineering tasks, suggesting a strong potential for future integration into automated analysis pipelines.