Edge Computing Security: Threats and Countermeasures in Edge Networks
Main Article Content
Abstract
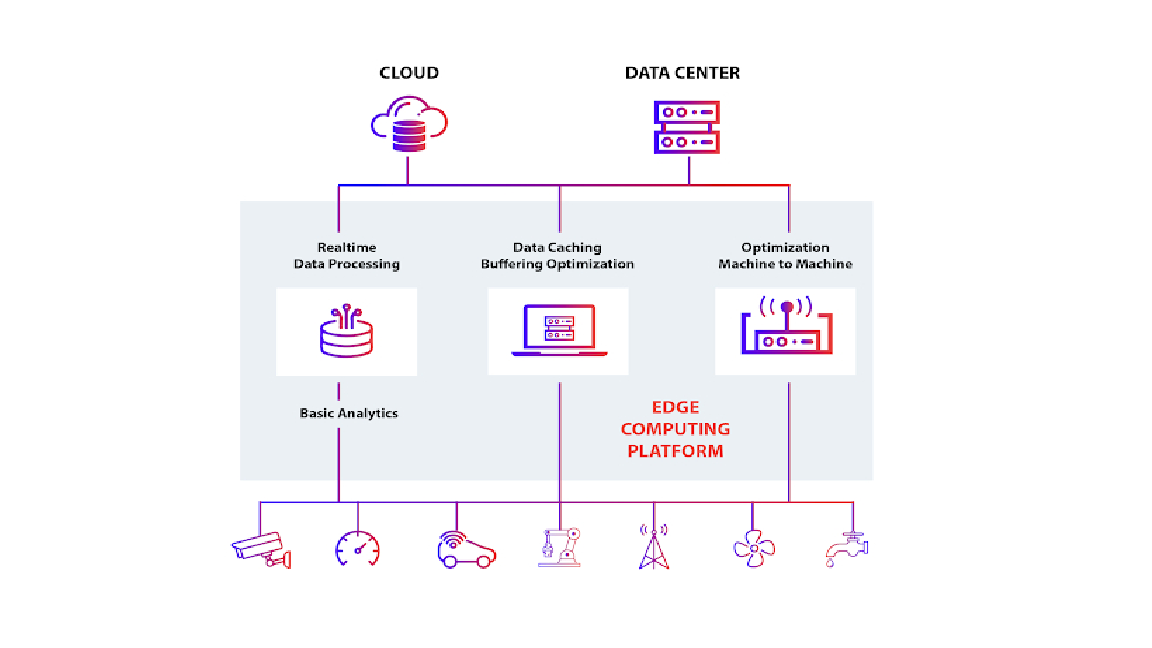
Edge computing has emerged as a transformative paradigm, enabling low-latency processing and real-time decision-making by decentralizing computation closer to data sources. However, the distributed nature of edge networks introduces significant security challenges, including data breaches, unauthorized access, and sophisticated cyberattacks targeting resource-constrained edge nodes. This paper provides a comprehensive analysis of security threats in edge computing, categorizing them into device, network, and application-level vulnerabilities. Additionally, we explore state-of-the-art countermeasures, including lightweight encryption schemes, secure authentication protocols, and AI-driven anomaly detection. By highlighting recent advancements and open research challenges, this study aims to guide the development of robust security frameworks for future edge networks.